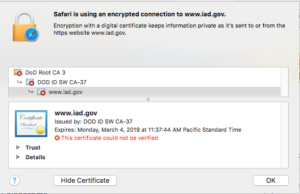
Recently, I wanted to read about the NSA’s Commercial National Security Algorithm (or CNSA) Suite, which is their replacement to the Suite B algorithms. The web site for the CNSA Suite is https://www.iad.gov/iad/programs/iad-initiatives/cnsa-suite.cfm, but if you go there now on a Mac, you’ll probably get a security warning. The reason is, this web site uses a certificate issued by the DoD, and I didn’t have them installed. How did I get them installed? Read on!
To be sure I’m going to the right place, I needed to securely download the DoD’s roots, and then trust the appropriate one. This is not the easiest thing in the world, because alot of the sites which have the DoD roots are either non-Government sites (which I don’t want to trust), or are Government sites that use the DoD CA (which makes trusting them a catch-22).
The NSA’s web site has this text:
Please visit the Information Assurance Support Environment (IASE) site to download the DoD Root CA Certificates. Select the Trust Store tab and choose the latest InstallRoot: NIPR Windows Installer.
This points you in the right direction, but not to the exactly-right thing (for one thing, I’m not running Windows). You do need to browse to https://iase.disa.mil/pki-pke/Pages/tools.aspx, but what you’re actually looking for is called PKI CA Certificate Bundles: PKCS#7.
Download the “For DoD PKI Only” ZIP file (as of publication, the version number is 5.3). You’ll end up with a folder containing eight files. Four of the files contain the phrase “Root_CA”, and end with “.p7b”. Those are the four files we will be needing.
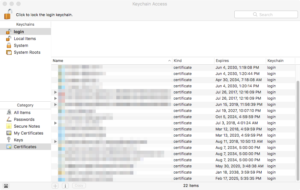
To install the certs, you’ll be using the Keychain Access application, which is an application that lives in the Utilities folder (which lives in the Applications area). Launch it, and go to your “login” keychain.
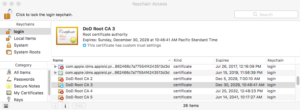
The “login” keychain is the one for your specific account, and the “Certificates” category shows all the certificates that you have added (or which have been added for you).
Next, double-click on each of the four .p7b files that we identified above. Or, drag the four .p7b files into the Keychain Access program. You’ll see your certificates list EXPLODE with DoD certs!
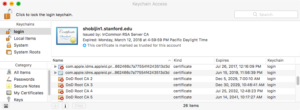
The four certs that we want are named “DoD Root CA” followed by a number (2, 3, 4, or 5). The other certs are intermediate certs; Safari does not need them, so you should delete all of the “DOD EMAIL”, “DOD ID SW”, and “DOD SW” certs. Once you delete those, your list will be much smaller!
Now, macOS (and Safari) has the CA certs, but the certs are still not trusted. This is a good thing; if you are concerned about trusting a US Government CA, well, right now you aren’t. You can turn trust on and off whenever you want.
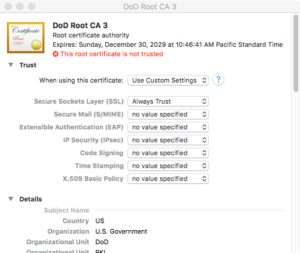
To enable trust, double-click on the appropriate CA, expand the Trust section, and choose how you want to trust the CA. Since I’m using Safari, I am changing the SSL entry to “Always Trust”.
When you close the window, you’ll be asked for your password, and then your changes will be saved. You’ll also know that you did it correctly when Keychain Access says that the CA is trusted.
You can now browse to the web site (in Safari or Chrome), and no warnings should appear. Once you are done, you can go back into Keychain Access and remove the trust settings.
Good luck!



Perfect. Seriously, thank you for the great step by step
Perfect. Thank you for that tutorial. The current version of the bundle is 5.4
This helped me…thank you.